As crypto expansions in esteem, the items in your wallet will turn out to be more important and, thusly, prey for tricksters. So how might you safeguard your resources in the Web3 space? Peruse on to find a few safeguards you can take to guarantee pariahs can’t get close enough to your crypto wallet.
Basic safety rules to navigate web3
Dapps like Uniswap, Axie Boundlessness, OpenSea, etc can be gotten to through dapp programs or Web3 wallets like Metamask. While communicating with these applications, clients can accidentally give tricksters express admittance to their wallets.
However, when you interact with dapps these dapps tap straight into your wallet. You are the one approving all actions.
Once this happens, scammers will not hesitate to transfer your funds to their own wallet, leaving you empty-handed. Therefore, it’s important to learn all you can about wallet safety. Let’s go through a couple of important points below.
1. DYOR before investing
Doing your own examination is web3’s most essential counsel – and the one that is generally effortlessly misjudged. It’s very simple to purchase tokens that somebody on the web says it’s a jewel. However, how could you indiscriminately trust a more peculiar’s perspective?
Try not to trust, check.Prior to putting your crypto in an up and coming task, dive profound into its site, Twitter (X) account, Disunity server, how connected with its local area appears, the designer group behind it, etc. Ensure you just interface your wallet to the dapps you have checked yourself.
2. Beware of what ads you click on
Never click on joins from unidentified sources; forever be careful about Google or virtual entertainment promotions for crypto administrations. In any case “genuine” the promotions appear to be, you might be checking out at a copycat of the first undertaking’s site or even a totally phony one. All things being equal, go to the venture’s true site and check whether such a drop or deal is accurately promoted by the authority media.
Also, Web3 powerhouses frequently advance undertakings on their authority virtual entertainment accounts that clients actually should be wary about. Here and there, their records have been hacked, and trick content is being shared without their assent. To put it plainly, consistently stay alert.
3. Always use 2FA, but never use SMS
Through friendly designing strategies, programmers can overwhelm your telephone membership. They just behave like they are you, and enact a new sim card. When they gain admittance to your telephone number, each stage that utilization two-factor approval (2FA) with SMS, will become helpless.
Accordingly you ought to never utilize SMS, yet rather depend on authenticator applications like Authy, Google’s Authenticator and other comparable ones.
4. Keep the token approval list empty
Interfacing with savvy contracts, dapps, and robotized market creators will cause you to endorse a wide range of connections. Nonetheless, such endorsements could allow your wallet to stay uncovered. In some cases, you may not realize that you cooperated with phishing joins that subvert the security of your wallet.
It's vital for keep your symbolic endorsement list as unfilled as could really be expected.All things considered, you can choose to collaborate with confided in connections and shrewd agreements as it were. Or on the other hand generally check for the rundown of shrewd agreements with admittance to any of your wallets and feel free to disavow them utilizing the essential instruments.
Revoking access to your wallet
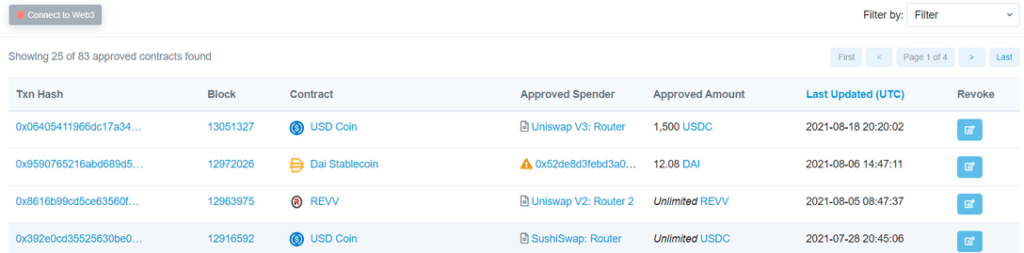
For tokens on the Ethereum organization, utilizing Etherscan assists you with knowing the quantity of brilliant agreements you have endorsed on your wallet. The Etherscan instrument is an information aggregator for all tokens fabricated through the ERC20 standard. So you can constantly get to see progressing exchanges on each ERC20 token.
Beside that, this is likewise a helpful instrument for evaluating your symbolic endorsements list. Through Etherscan you can renounce admittance to your wallet. At the point when you repudiate admittance to your wallet, the following time you enter that dapp you should support access once more. Nonetheless, your tokens will not be gone. No problem. Presently, we should get to the essence of the entire talk.
How to check for the approved token list
- Open Metamask, and make sure you’re logged in. Click the wallet address to copy it.
- Go to the Token Approval Checker on Etherscan. The service is currently in beta and can be found once you log in to Etherscan > More > Tools > Token Approvals.
- Paste your wallet address > press search
- The page will now show all approved smart contract interactions with that particular wallet.
- Click the “Connect to Web3” button to connect Etherscan to your active wallet in Metamask.
- Once connected, you can click the “Revoke” button on the right side to make sure a certain dapp no longer has access to your wallet. Keep in mind, there are gas fees involved in revoking access. However, the choice between spending $5 or losing $5,000 is presumably pretty easy.
In a similar fashion, users can revoke token approvals on Binance Smart Chain and Polygon as well. Simply follow the links below, and go through a similar process as described above:
5. Have multiple wallets for different purposes
Try not to keep all eggs in a similar container. That is a typical misstep web3 voyagers novices or not frequently make – however that is not difficult to address.
While exploring web3, you’re probably going to at the same time interface your wallet with different undertakings. Furthermore, on the off chance that you truly do neglect to purge your symbolic endorsement list or to profoundly explore a venture prior to interfacing and succumbing to a trick – you’re cool since every one of your resources will be isolated into various wallets.
The most fundamental rendition of this is having a cool wallet – like a Record – to securely store your NFTs and crypto of higher worth, similar to a safe. It’s significant not to involve it as a program wallet you’d use to trade tokens and interface with any task.
On the off chance that you in all actuality do get hacked, just a single wallet will succumb rather than your whole portfolio.
Closing words
Obviously, one can never be too sure of the security of one’s wallets; you just have to assume the worst and act accordingly.
Getting your wallet drained is a bad experience and might set you back thousands of dollars. Reviewing and revoking tokens via any of the tools mentioned above is an effective way to protect your wallets from scammers. Adding another weapon to your arsenal in the battle against scammers.








